SYNOPSIS
Dramatic changes in the economy are arriving at a time when IT infrastructures are becoming more dynamic with the use of virtualization, cloud computing, and distributed information flows across organizational boundaries. IT and business professionals have many options for spending on security, but it is vital to understand these options in relation to their business strategy and operational constraints.
The Shortcut Guide to Prioritizing Security Spending provides a framework for IT professionals and business managers grappling with challenges from an economic downturn to rapidly changing technology options. Any IT professional expected to maintain effective security practices in this increasingly complex environment will find this guide to be an invaluable resource. Topics include leveraging opportunities created by the changing economy, protecting business operations while maintaining staff efficiencies, and making judicious use of virtualization, cloud computing and other technologies for optimizing service delivery.
CHAPTER PREVIEWS
Chapter 1: Optimizing Business-Driven Security
Today we are witnessing a confluence of technical, social, and business trends that shape the challenges we face in information security. Fortunately, these same trends contain the means for addressing the challenges. Monolithic applications have given way to component-based systems based on Service-Oriented Architectures (SOAs) and mashups. Virtualization and cloud computing are changing the nature of the data center with a shift from dedicated hardware for applications to a shared hardware model. Social drivers include an increased awareness of risks to personal information and an associated undermining of trust in organizations’ ability to protect that information. The current economic slowdown is a dominant business concern for obvious reasons but it has less obvious implications for information security as well. How are businesses to manage security spending in such a dynamic and multifaceted environment?
This eBook, The Shortcut Guide to Prioritizing Security Spending, provides a framework for understanding today’s information security environment and selecting an optimal set of technologies, policies, and practices to meet the needs of your particular business. This guide consists of four chapters, each of which addresses a key part of the overall framework:
- Chapter 1 examines how the slowing economy creates opportunities as well as challenges for businesses. The chapter examines security as it relates to topics such as the dynamic workforce, evolving technologies, and compliance issues. It also considers opportunities provided by cost optimizations, business consolidation, and competitive advantages enabled by improved security.
- Chapter 2 focuses on protecting business operations and optimizing staff efficiency. Business operations are considered with respect to preserving the confidentiality, integrity, and availability of information and services. Staff efficiency includes both overall productivity in an organization as well as security administration efficiencies.
- Chapter 3 considers several key technological trends that must be accommodated within a security management framework, including virtualization, cloud computing, distributed information flows, application security, and Web 2.0 technologies.
- Chapter 4 describes a multi-phased approach for prioritizing security spending. Starting with an assessment of the business environment, the process moves on to design and deployment issues followed by a discussion of implementation and management topics. The final phase considers education, a critical but sometimes overlooked practice in prioritizing security spending.
Chapter 2: Maintaining Effective Security Practices in an Increasingly Complex Environment
Infrastructure is a term we have adopted in information technology (IT) to describe the information assets of an organization, including hardware, software, data, and procedures. It is an apt term. After all, roads, bridges, and tunnels of a country’s transportation infrastructure enable the flow of people and goods while IT infrastructure enables the flow of information. Both are essential for modern commerce. Even so, we do not have to push the analogy too far though to see it break down.
Roads and bridges are built to last for decades with occasional maintenance work. A 10-year-old map may not be perfectly accurate but it is probably pretty close. Although transportation infrastructure is relatively static, information infrastructure is anything but. Desktop devices are updated every few years, and servers even more frequently. Software seems to be in a constant state of change as it is modified and redeployed to meet changing business requirements. Even the technologies that underlie infrastructure change. The advent of virtualization, inexpensive storage, and ubiquitous high-speed networking has provided the foundation for cloud computing. Smartphones and wireless communications are changing the way businesses communicate and collaborate with employees, business partners, and customers. Changes in IT infrastructure are not limited to smaller computers or less expensive network equipment: new infrastructure is changing the ways we design systems and deliver services.
The dynamics of IT bring benefits and challenges. Take, for example, the need to provide customer support. In the past, customers would expect to pick up a phone, call a toll-free number, and talk with a customer representative about a problem with a new product or a question about the customer’s account. Today, expensive customer support call centers have been replaced with voice response telephony, online self service support, and even collaborative forums in which customers help each other. These kinds of unquestionable efficiencies introduce problems that did not exist prior to the advent of e-business. Thieves can steal customer information and intellectual property without ever setting foot in a company’s offices or stores. Disgruntled employees can sabotage an application and corrupt databases from their desks. Unsuspecting customers can fall victim to a phishing scam that uses your business as bait. The increasingly complex IT environment requires sufficiently adaptive security management practices to realize the benefits of change without falling victim to it.
This chapter considers the fundamental requirements for protecting business operations with an emphasis on three over-arching goals:
- Protecting the confidentiality of information by preventing data loss
- Preserving the integrity of information by preventing malicious operations on data
- Ensuring the availability of services by maintaining infrastructure efficiency
These three goals are subject to the same demands for efficiency as any other business operation. For that reason, this chapter will also address the need for maintaining both overall business operation productivity and security administration efficiencies.
A combination of technologies and practices can serve to protect assets and maintain operational efficiencies. Let’s start our examination of that topic with a look at basic requirements for protecting business operations.
Chapter 3: Security and the Dynamic Infrastructure
Information security practices have evolved along with advances in hardware, software, and systems architectures. Security in mainframe and mini-computer environments was dominated with issues of physical access and user account management. Distributed architectures introduced the need for authentication and authorization mechanisms that accommodated multiple clients and servers. Early widespread use of the Internet led to the adoption of perimeter security techniques, such as network DMZs. Today, those measures must be augmented with multiple layers of defenses on individual devices and network security controls, such as intrusion prevention systems (IPSs) and content-filtering applications. This pattern of changing security practices shows no sign of abating.
A number of technologies and advances in system designs are introducing opportunities to improve security as well creating the need for additional security measures to ensure the continued protection of the confidentiality, integrity, and availability of information resources. This chapter will examine four sources of change in information security:
- Virtualization
- Cloud computing
- Distributed information flows
- Web 2.0 technologies
Together, these technologies are enabling a more dynamic infrastructure than we have previously had to manage. Virtual servers can be provisioned and moved into production faster than physical servers. On-demand computing and storage resources in the form of cloud computing is changing the way we handle peak demand periods and reducing barriers to expansion, especially with regard to the need for capital expenditures. Businesses’ relentless drive for efficiency coupled with improvements in workflows and information interchange are leading to distributed information flows that cross organizational boundaries. Rich Internet applications are bringing desktop application functionality to the Web but at the expense of an increasingly complex set of software components. All these technologies provide new degrees of flexibility in how we configure and manage IT infrastructure. With a focus on keeping a dynamic infrastructure secure, we will examine each of these technologies with an eye toward discerning the security implications of each.
Chapter 4: Best Practices for Prioritizing Security Spending
Businesses and other organizations face difficult challenges when protecting their information assets and infrastructure. As we have discussed throughout this guide, the combination of security threats, constantly evolving IT technologies, and limited resources require us to prioritize security spending. There are so many factors that can influence our choices, it helps to first clearly articulate our goal and then develop a methodology for meeting the goal.
We start with assuming our goal is to implement security practices that align with business strategy. Security is not an end in itself and it is not the driving goal. That assertion may sound a little strange especially in a book about security, but it actually addresses the heart of the problem in prioritizing security spending.
We do not implement security controls for the sake of having controls. If we did, we would disconnect our computers from the Internet, severely limit physical contact with servers, and implement access controls so stringent that even if potential users somehow gained access to a system they could not do any substantive work with applications or data. Once again, security is a means to an end, not an end in itself. Our real goal is to support the business strategy of the organization. Formulating that strategy is outside the scope of security practices, although, as we have seen throughout this guide, security concerns can influence that strategy and constrain options for implementing it.
There are so many options to choose from when considering how to best allocate security spending that a methodology for organizing and categorizing those decisions can be a significant aid to the process. The methodology advocated in this book is depicted in Figure 4.1. The methodology is similar to other IT life cycle-based methodologies that start with understanding business requirements and follow through multiple stages to implementation and maintenance.
The methodology also includes an education component, which is not typical of other life cycle-based methodologies. This education is unlike the training provided to administrators or end users of a new application, which tends to focus on particular functionality of a system. The purpose of security education is to develop an awareness of security threats and how to detect and avoid them. It is important that all stakeholders understand fundamentals of security threats because the specifics are constantly changing. Email viruses were more of a problem 10 years ago than today but malware has not gone away; it instead uses additional methods to propagate.
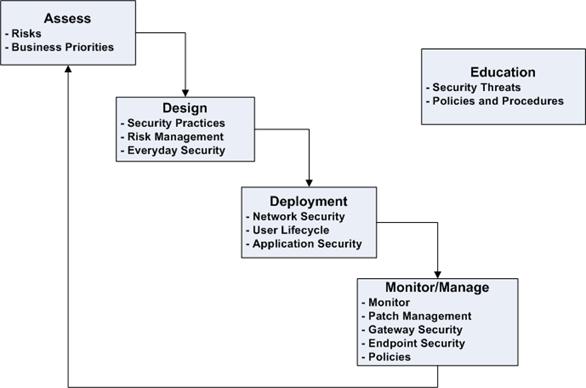
Figure 4.1: A methodology such as the model shown here helps with prioritizing security spending. The process begins with assessing risks and business priorities followed by steps to design, deploy, and manage security controls. Note this process is cyclical and knowledge gained in the process can help guide later assessments. Education is a key element of the methodology and spans the other stages.







